In the context of web security, a parameter refers to any input or value that is sent to a web application through a URL or a form. These parameters can be anything from a username and password to more complex values, and they play a critical role in determining how the application behaves.
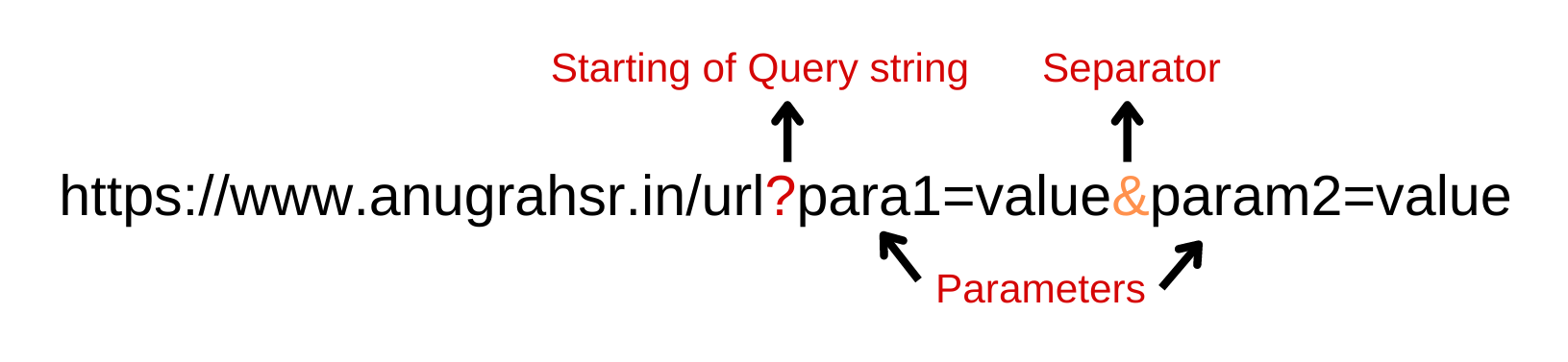
When it comes to finding security vulnerabilities in web applications, one of the most important things to do is to identify as many parameters as possible. This is because each parameter represents a potential entry point for an attacker to exploit.
By finding more parameters, security researchers, penetration testers and bugbounty hunters can significantly increase the attack surface of an application. This, in turn, allows them to identify a wider range of potential vulnerabilities, including things like SQL injection, cross-site scripting, and more.
Now that we understand the importance and drive behind identifying Hidden Parameters, let's explore various methodologies and tools to perform parameter discovery.
TLDR;
- arjun https://github.com/s0md3v/Arjun.git
- paraminer https://github.com/PortSwigger/param-miner
- paramspider https://github.com/devanshbatham/ParamSpider
- x8 https://github.com/sh1yo/x8#test-site
- gap https://github.com/xnl-h4ck3r/GAP-Burp-Extension
- ReconAIzer https://github.com/hisxo/ReconAIzer
Methods and tools for parameter discovery:
Now let's find all the hidden parameters unlinked, unreferenced or unintentionally/accidentally open for use?
Arjun
Repo: https://github.com/s0md3v/Arjun
Creator: S0md3v
Arjun is a tool that can find valid HTTP parameters for URL endpoints in web applications. It has a default dictionary of 25,890 parameter names and can make 50-60 requests to the target in less than 10 seconds. Arjun supports various types of requests and can handle rate limits and timeouts. It also allows exporting results to various file formats and can passively extract parameters from JS or external sources.
Installation
#with pip
pip3 install arjun
#with repo
git clone https://github.com/s0md3v/Arjun.git
cd Arjun
python3 setup.py install
Usage:
#Scan single url
arjun -u https://www.example.com/endpoint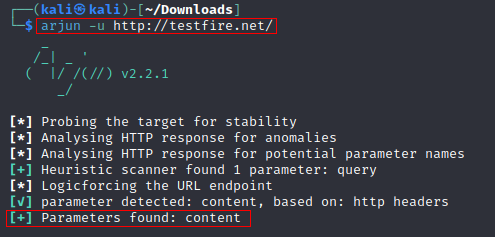
Arjun looks for GET method parameters by default. All available methods are: GET/POST/JSON/XML
#specify the request method
arjun -u https://www.example.com/endpoint -m POST
#scan a list of targets
arjun -i targets.txt
#Use custom wordlist
arjun -u http://www.example.com/endpoint -w parameters.txt
#export to Burp
arjun -u http://www.example.com/endpoint -oB 127.0.0.0:8080
Arjun has more features which you can read it here:
Here are some reports where arjun helped bugbounty hunters earn some $$$$
X8
Repo: https://github.com/Sh1Yo/x8
Creator: Alexander Mironov(sh1yo_)
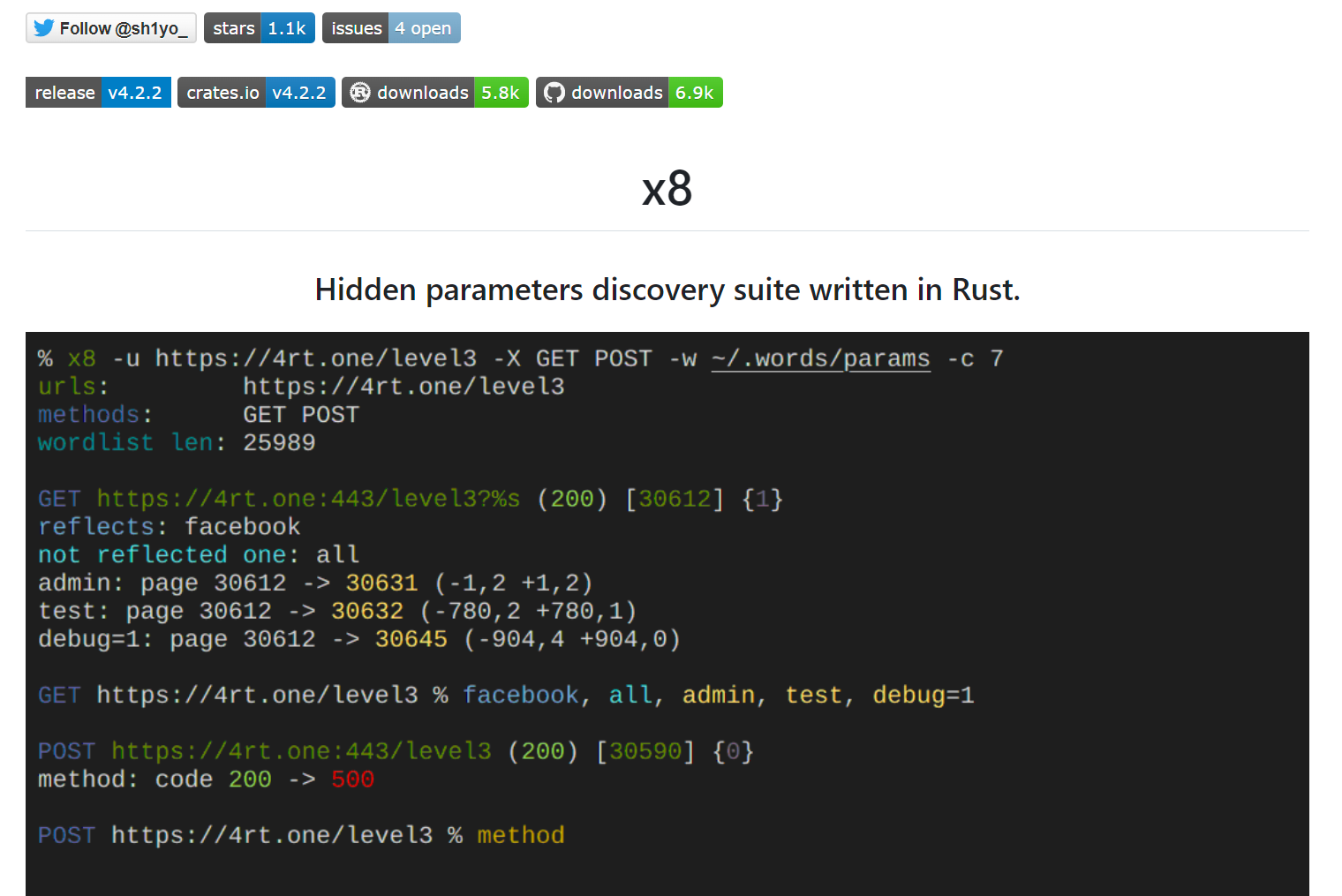
x8 is a Hidden parameters discovery suite written in Rust that helps identify potential vulnerabilities or interesting functionality missed by other testers. It offers fast and flexible request configuration using templates and injection points. x8 is highly scalable and can check thousands of URLs per run. It achieves high accuracy through line-by-line comparison of pages, comparison of response codes, and reflections. The tool can discover parameters with non-random values and is highly configurable with a wide range of options. Additionally, x8 achieves almost raw requests through external library modification.
Installation
#via cargo install
apt-get install cargo
cargo install x8
#from source code (rust should be installed)
git clone https://github.com/Sh1Yo/x8
cd x8
cargo build --release
Usage:
#Single URL
x8 -u "http://www.example.com/" -w <wordlist>-u specify the URL and -w specifies the wordlist to be used
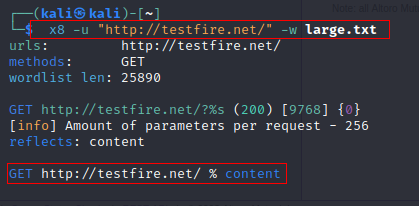
#specify the request method using -X
x8 -u "http://www.example.com/" -w <wordlist> -X GET POST#scan a list of targets with -u
x8 -u targets.txt -w <wordlist>x8 can be integrated with Burp suite using the Custom Send To extension from BApp store.
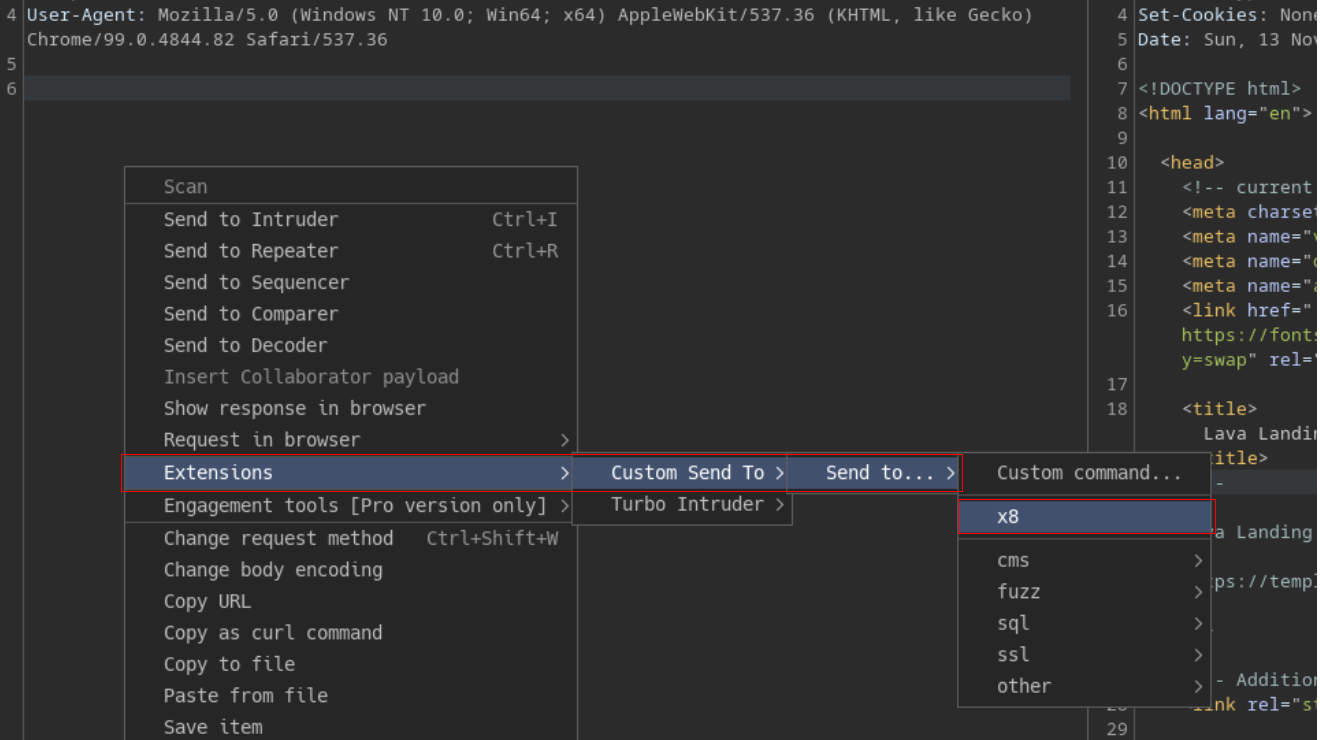
Burp Suite integration can be found here:
Para-miner
Repo: https://github.com/PortSwigger/param-miner
Creator: PortSwigger
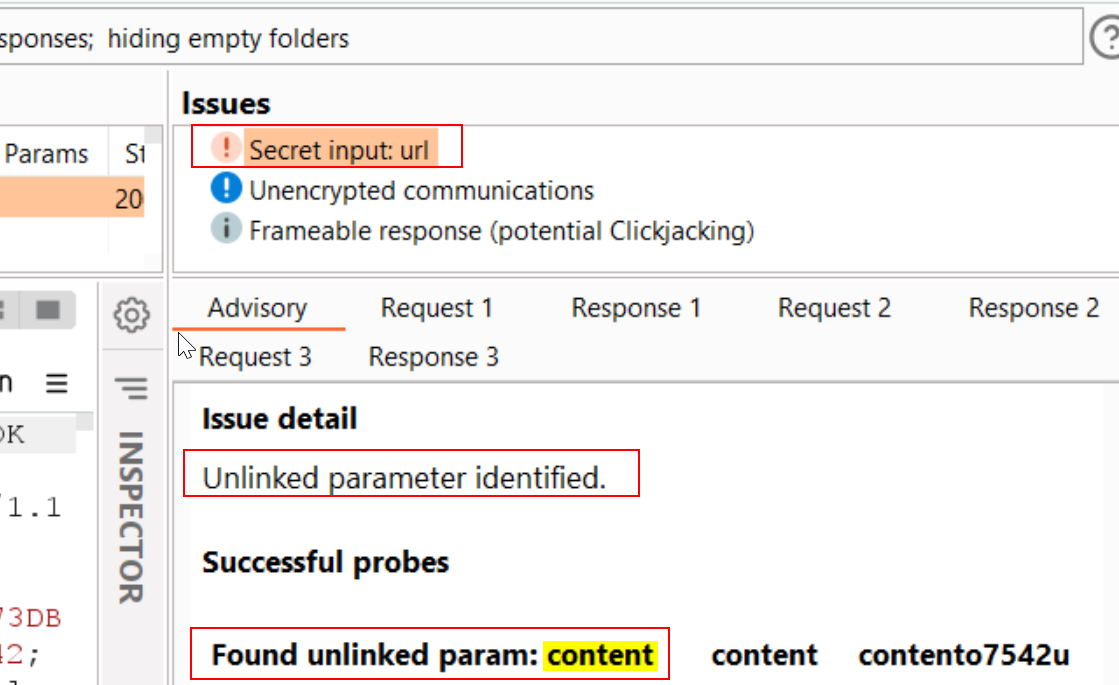
The extension is designed to identify hidden and unlinked parameters, with a specific focus on finding web cache poisoning vulnerabilities. It uses advanced diffing logic from Backslash Powered Scanner, along with a binary search technique, to guess up to 65,000 parameter names per request. The extension includes a built-in wordlist, and also harvests additional words from all in-scope traffic to improve its accuracy.
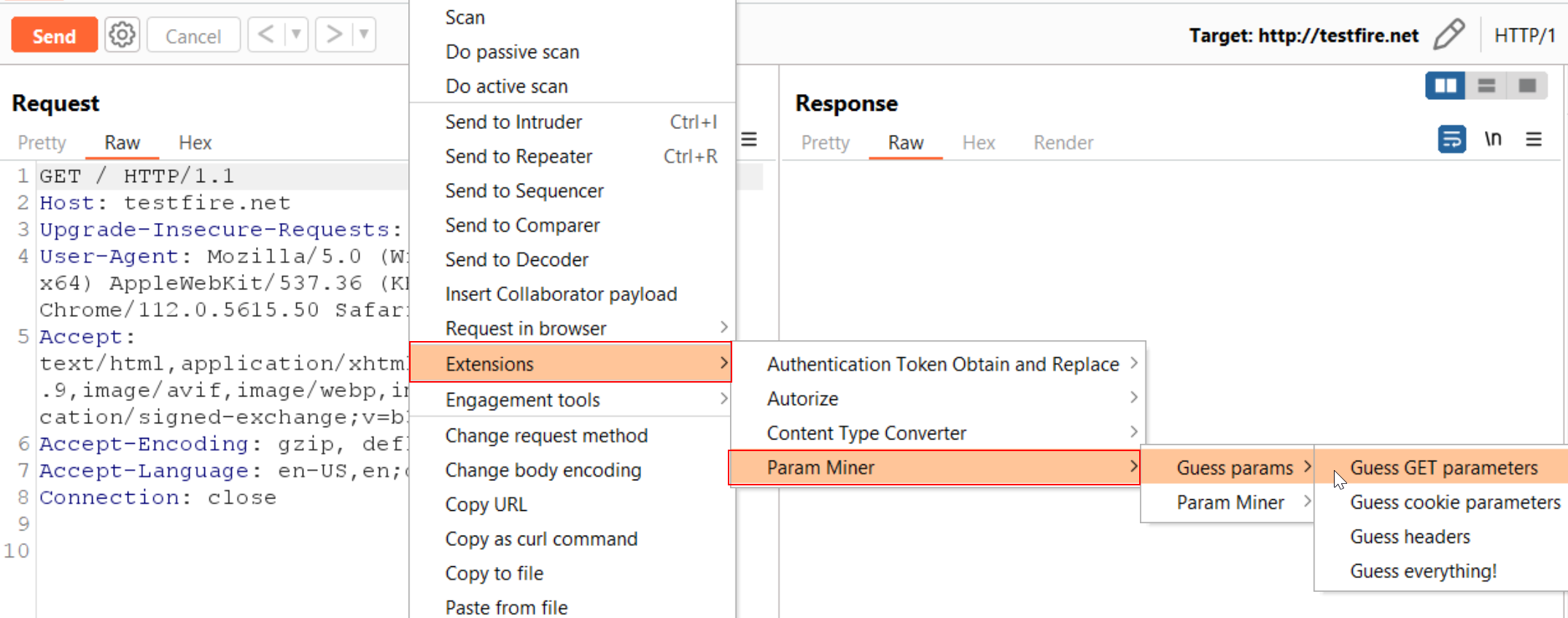
Usage
Extensions -> Param Miner -> Guess params
Para miner indetified the unlinmked parameter content
Paraminer is powerful for discoving web cache poisoning issues, you can read about it here:
Read this blog to understand how Nagli used para-miner to get cool bounties and bugs
- Poisoning your Cache for 1000$ - Approach to Exploitation Walkthrough
- Mass Assignment exploitation in the wild - Escalating privileges in style
Paramspider
Repo: https://github.com/devanshbatham/ParamSpider
Creator: Devansh(0xAsm0d3us)
ParamSpider is a tool designed to mine parameters from web archives, including subdomains, of a specified domain. It can exclude URLs with specific extensions and saves the output results in a clear and organized manner. ParamSpider operates without interacting with the target host, making it a non-invasive tool for parameter discovery.
Installation
git clone https://github.com/devanshbatham/ParamSpider
cd ParamSpider
pip3 install -r requirements.txt
python3 paramspider.py --domain hackerone.com
Usage:
Simple scan
$ python3 paramspider.py --domain target.com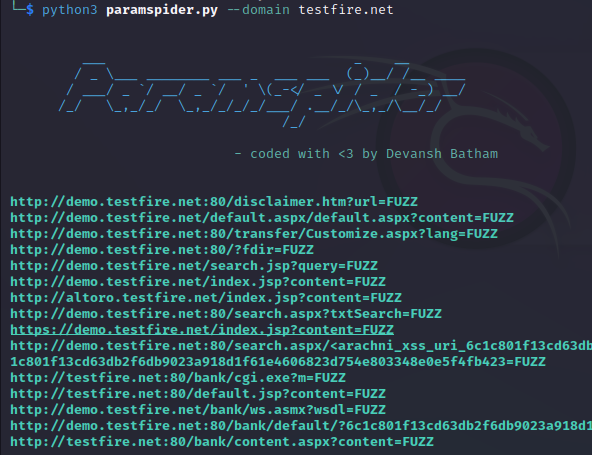
Excluding urls with specific extensions
$ python3 paramspider.py --domain hackerone.com --exclude php,jpg,svg
Finding nested parameters
$ python3 paramspider.py --domain hackerone.com --level high
Saving the results
$ python3 paramspider.py --domain target.com --exclude php,jpg --output target.txt
Custom placeholder text (default is FUZZ)
$ python3 paramspider.py --domain target.com --placeholder FUZZParamspider can be paired up with ffuf and gf tools for maximum efficiency!
GAP-Burp-Extension
Repo: https://github.com/xnl-h4ck3r/GAP-Burp-Extension
Creator: xnl-h4ck3r
The GAP-Burp-Extension is an updated version of the original getAllParams extension for Burp. It not only identifies potential parameters but also discovers potential links to test these parameters on. Additionally, it creates a target-specific wordlist for fuzzing purposes. Users can access the full Help documentation on the GAP tab or by visiting the GitHub repository.
Installation
- Download the GAP.py and requirements.txt from this project and place in the same directory.
- Install Jython modules by running java -jar jython-standalone-2.7.3.jar -m pip install -r requirements.txt.
- Go to the Extensions -> Installed and click Add under Burp Extensions.
- Select Extension type of Python and select the GAP.py file.
Usage:
Extensions -> GAP
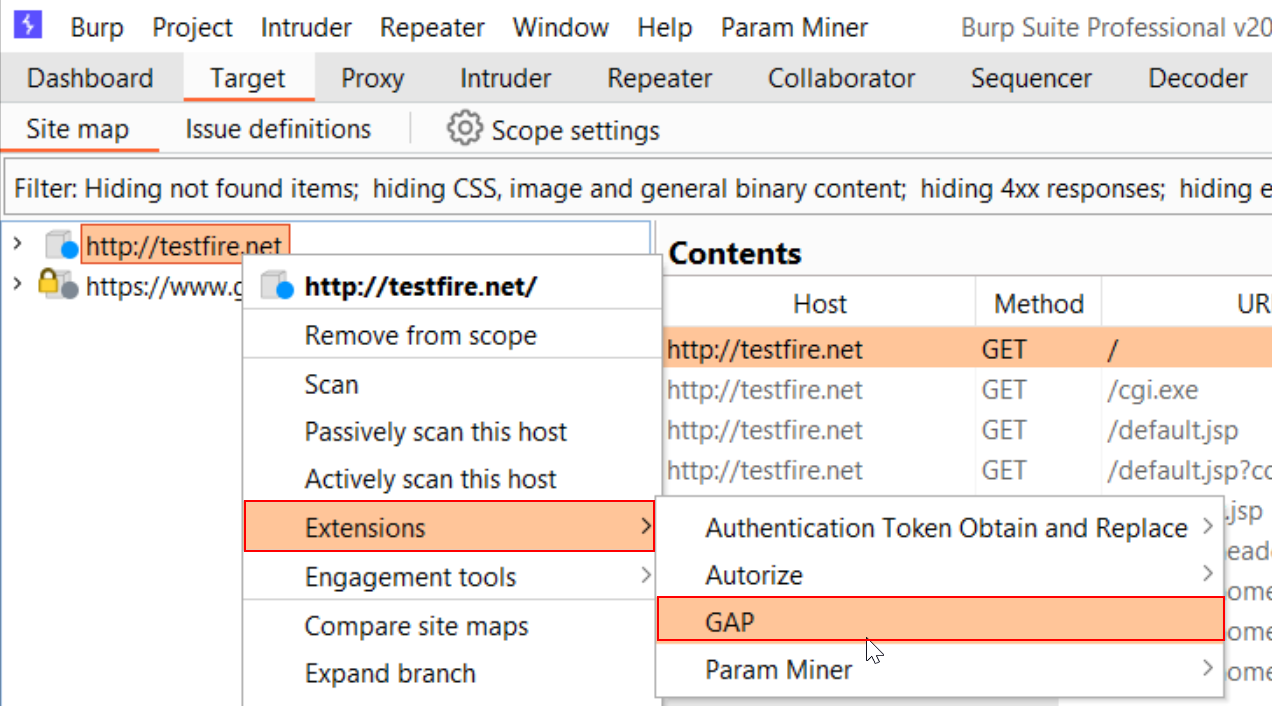
The results can be found in the GAP tab
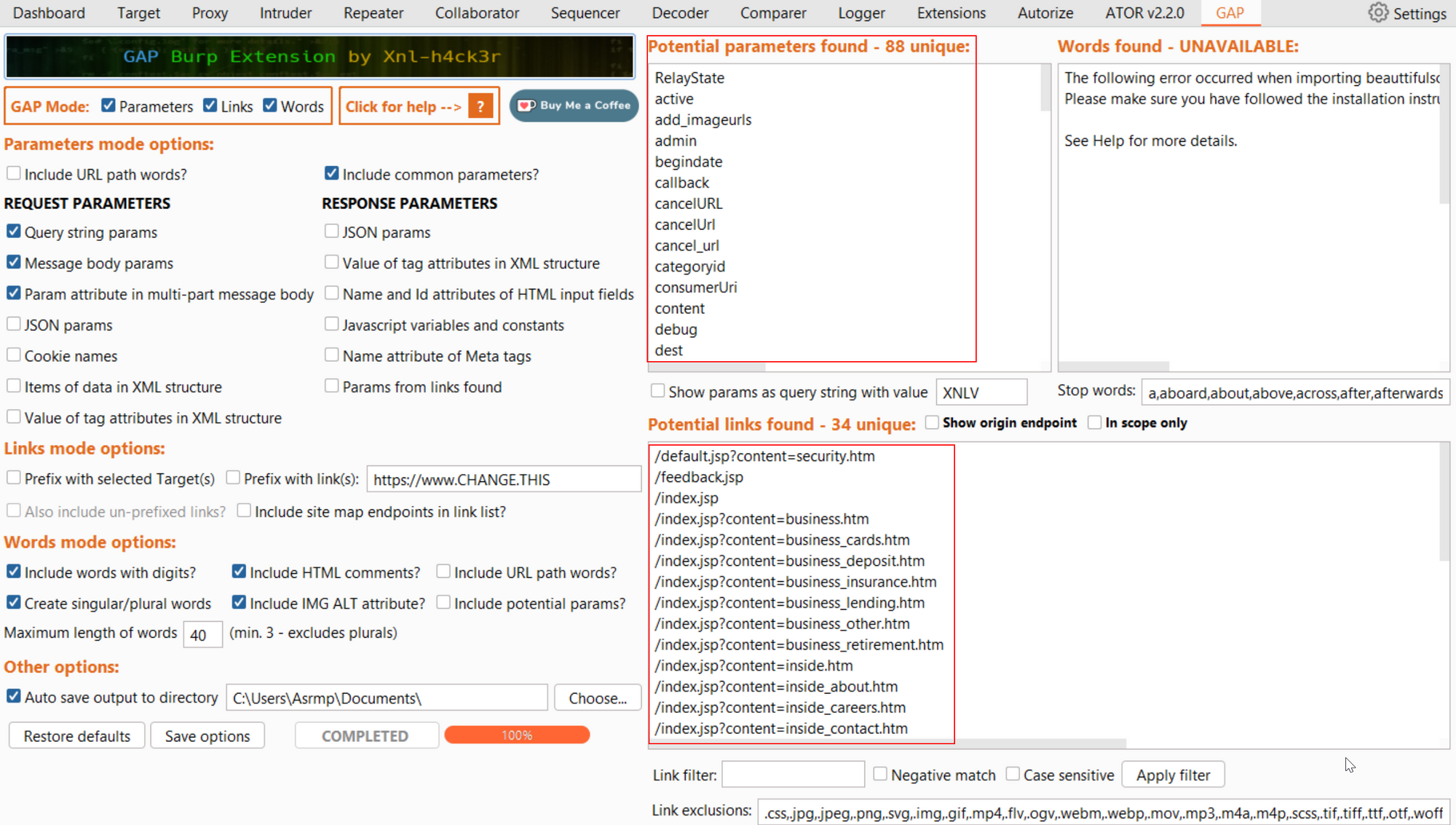
GAP is a powerful tool and burp extension that you should definity check out.
ReconAIzer
Repo: https://github.com/hisxo/ReconAIzer
Creator: hisxo

ReconAIzer is a Jython extension for Burp Suite that incorporates OpenAI to enhance the bug bounty recon process. This extension automates numerous tasks to assist security researchers in identifying and exploiting vulnerabilities. It can identify endpoints, params, URLs, subdomains, and more. The power of the GPT-3 in your burp!
Installation
- Download the ReconAIzer.v0.4.py
- Go to the Extensions -> Installed and click Add under Burp Extensions.
- Select Extension type of Python and select the ReconAIzer.v0.4.py file.
- On config page add the OpenAPI API key
Usage:
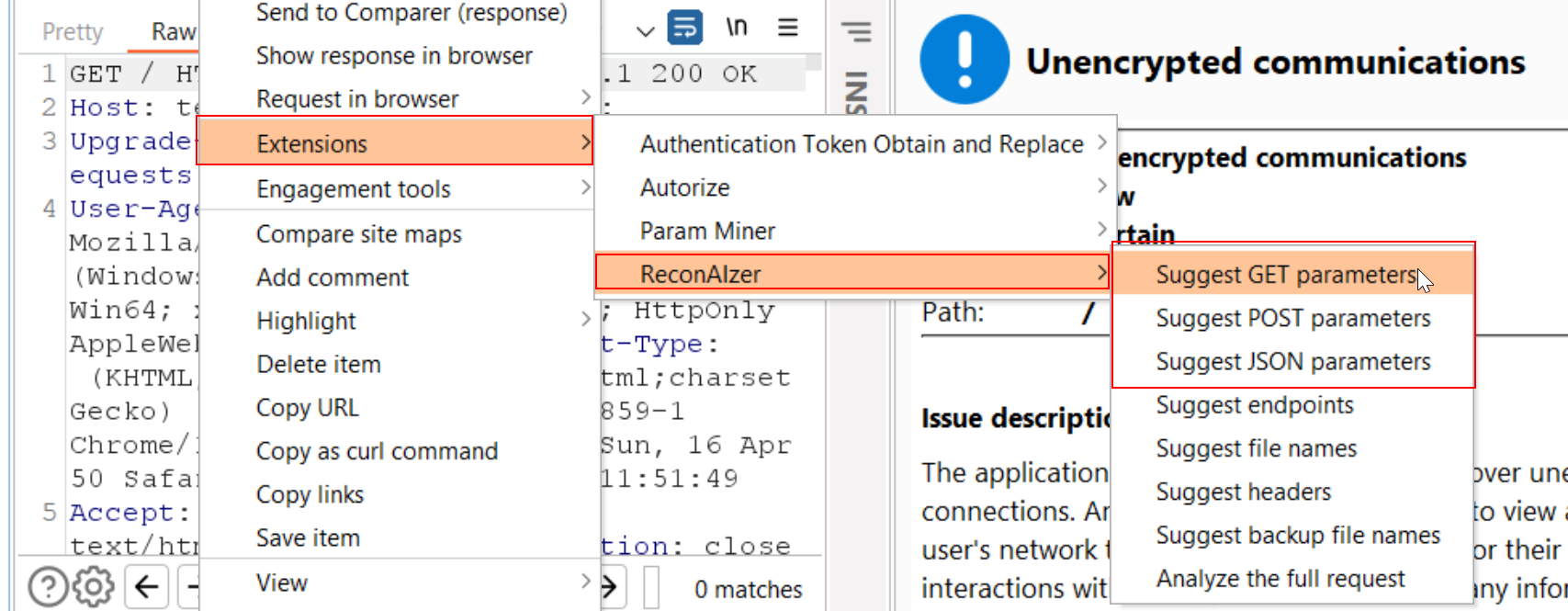
Extensions -> ReconAIzer -> Suggest GET/POST/JSON Parameters
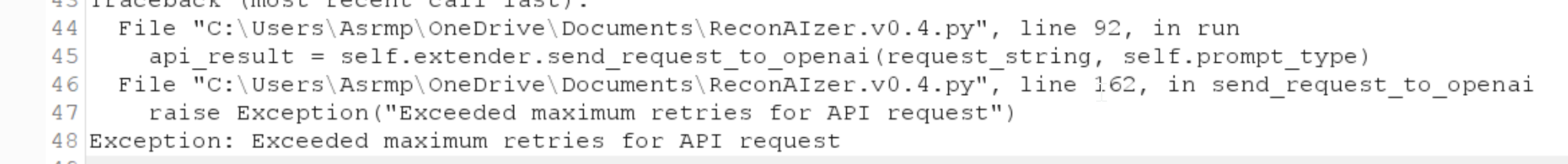
At the time of testing, i was getting the following error! I tried different API keys.
Still looks like a promising extension using OpenAI, play around with it.
So if you're looking to improve the security of your web applications, one of the best things you can do is to focus on finding and testing as many parameters as possible. By doing so, you'll be able to identify and address potential vulnerabilities before they can be exploited by attackers. Now you know how to find more parameters!
If you liked this blog and want too see such contents, Let me know in the comments and share it with your peers!



